
Whitepaper
Atlassian Cloud data protection
Executive summary
Data is your organization’s most important asset, but the risk of a potential data breach only grows at scale. Even with a dedicated security team, you need more resources behind you if you’re going to protect your data.
In Cloud, the responsibility for protecting your data is shared between you, Atlassian, and the companies who build and operate any Marketplace apps you use. In this whitepaper, learn about how we’ve optimized the Atlassian Platform with data protection capabilities in each layer to provide maximum protection, and how we’re empowering Marketplace partners to protect your data when you install apps.
Key takeaways
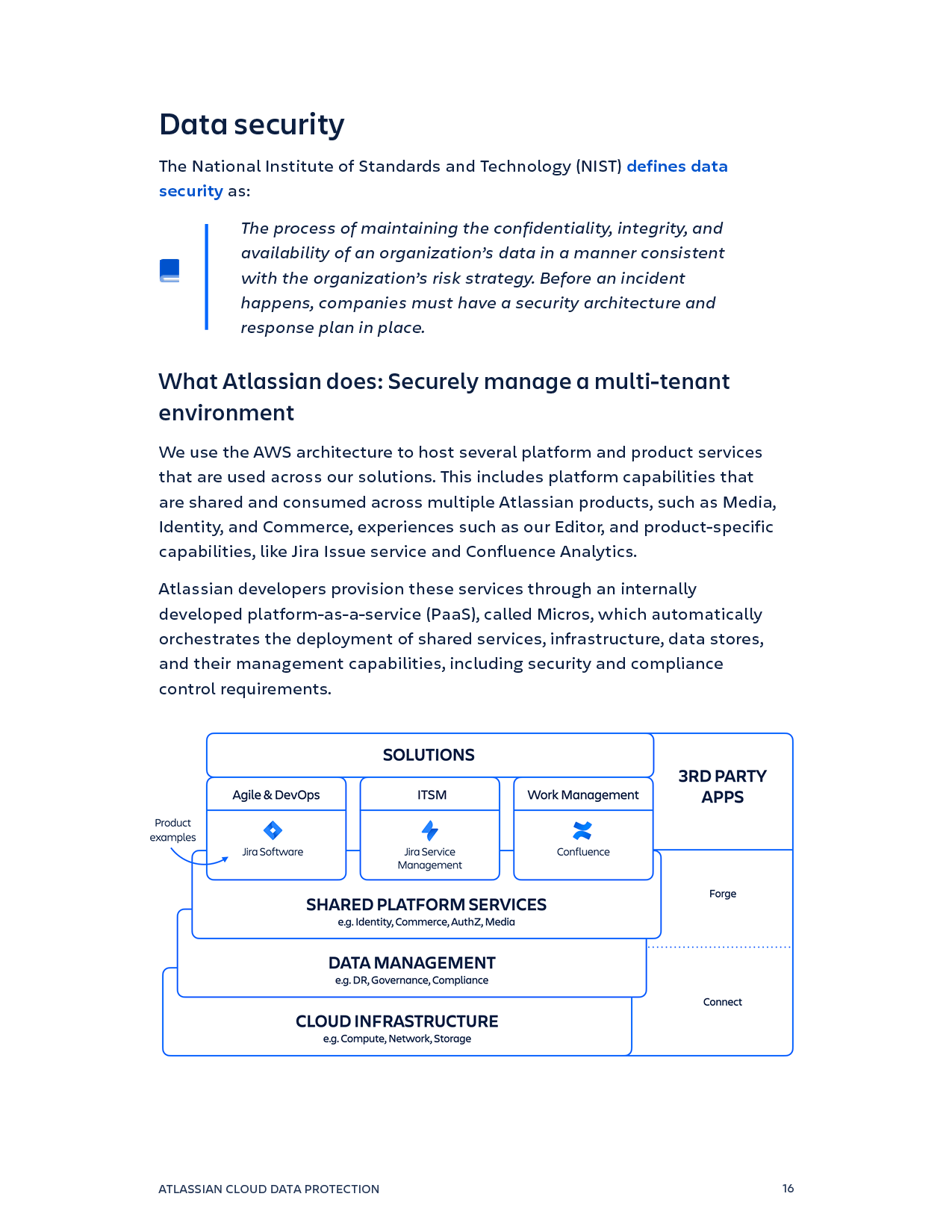
Data protection capabilities are built directly into the Atlassian Platform
Enterprise-grade cloud infrastructure ensures the reliability and recoverability of your data
Data protection controls ensure you and Atlassian can keep your data secure, private, compliant, and available
Centralized administration provides visibility into your instance to protect your organizations from threats
Atlassian and Marketplace Partners are working to increase app security, privacy, and compliance, and to help you more easily vet and manage apps
PDF content preview
Introduction
Data is the most critical asset to your organization, yet, it’s becoming increasingly more challenging to protect and secure. If data isn’t protected correctly, the cost of a data breach is costly. In 2022, IBM reported that the average cost of a data breach was 4.35 million dollars.
What are the challenges?
Managing complex and interconnected IT systems
Managing your IT infrastructure is a lot of work. The number of products and apps that teams use continues to grow. On average, enterprises use between 100 - 200 applications, with many of them managed by lines of business outside your IT department.
Regardless of ownership, these apps and products are used in concert so data can flow between them to enable collaboration between cross-functional teams. Complex, multi-app environments increase the attack surface and introduce risk due to varying levels of security across different apps.
Ensuring that only the right people can access data
As your organization grows, more people, devices, and applications access your data - increasing the risk of unauthorized access. Striking a balance between keeping people productive and narrowing access points only becomes more difficult.
Adapting to regulatory requirements
Industries and geographies have requirements that specify what controls must be in place to meet regulatory obligations and keep personal data safe. But the landscape is constantly evolving, and the requirements are a moving target that takes time to keep track of. Plus – these governing bodies are putting more onus on organizations like yours to prove compliance with these requirements.
Keeping sensitive data secure
Your company’s data is important, but some can be more sensitive, such as legal information or employee records. Correctly classifying data and applying appropriate safeguards is critical to protecting sensitive data like PII, credit cards, etc.
Recovering from outages
An outage's impact on an organization only increases at scale. On average, one minute of downtime can cost an enterprise $9,000. Multiplied by the total amount of downtime, an outage can cost hundreds of thousands of dollars.
But outages don’t just impact your revenue. They can also cause business disruptions, internal productivity loss, financial penalties, and litigation.
Detecting and responding to threats
You can’t control threats you can’t see. Your organization must have built-in threat detection, monitoring, and reporting features. Many products don’t offer out-of-the-box solutions, which requires organizations to manage additional products that add to their already exhaustive list of applications.
Evaluating Marketplace app security and privacy
Marketplace apps provide flexibility to customize and extend your complete solution. However, many apps are built and managed by third parties.
Installing an app requires a separate relationship with the company that offers the app. It’s important to vet the apps on your instance, as they may handle data differently than the product they’re extending.
Compounding these challenges are good and bad actors - people.
Overcoming these challenges isn’t impossible, but you need the right tools. That’s why we’ve specifically built Atlassian cloud products and solutions with the features and capabilities that you need to protect your data.
PDF preview

Access the full download
Atlassian Cloud data protection
